How to install and configure Applocker to improve Application Control & Security
AppLocker is a feature that gives you another Level of security
You can allow or deny access to software for a specific group of users.
The technology is old. However, it’s a tool that can be set up without complexity and helps you manage the applications from all the endpoints in your network.
Today, a lot of applications don't need administrator access to run. This is a threat to your environment.
While installing and configuring the AppLocker , you can significantly increase security and protect your data from any unauthorized access.
If you are thinking why to use AppLocker the answer is here.
You can use it to protect against unwanted software, software standardization, and software management.
If you want more details you can read the AppLocker policy use scenarios in Microsoft Docs.
Today I will install, configure, and Deploy the AppLocker through GPO to specific Servers.
Operating System Requirements
AppLocker can be deploy in
- All editions of Windows 10 version 2004 and newer including the KB 5024351.
- All Windows 11 editions including the KB 5024351.
- For Windows versions older than 2004 Group Policies deploy supported only for Enterprise and Server Editions.
- Policies deployed through MDM are supported in all Editions and versions.
- Windows Server 2012,2016,2019
So let's start !!
- Before start to implement AppLocker you must be know exactly which Applications must be allow to run.
- This is the most important step because if you try to apply AppLocker without note down what Applications must be allow then you will create lot of problems in your users and the daily operation of your company.
- In case that you are not sure 100% which is the Applications that must be allow you can use AppLocker in Audit Mode to identify all the applications.
How to enable AppLocker
-
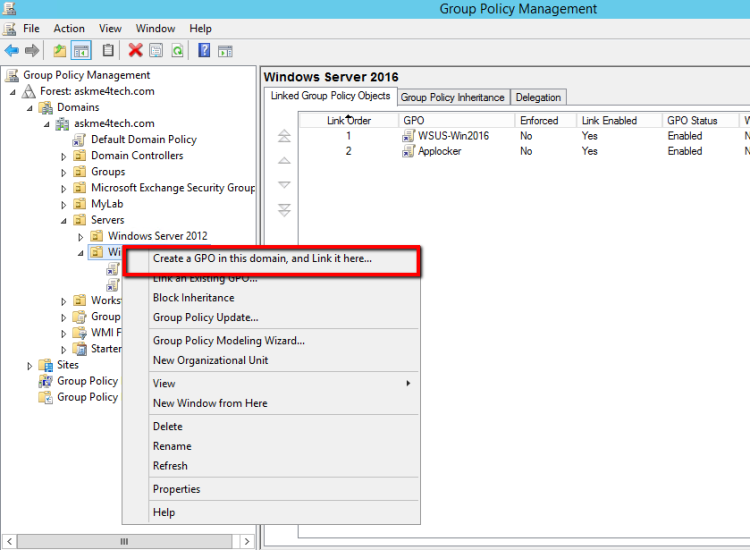
Login in the Domain Controller and open the Group Policy Management.
-
Right click in the Organization Until that you want to create the AppLocker Policy and select Create a GPO in this Domain and link it here.
- Type the preferred name and click OK
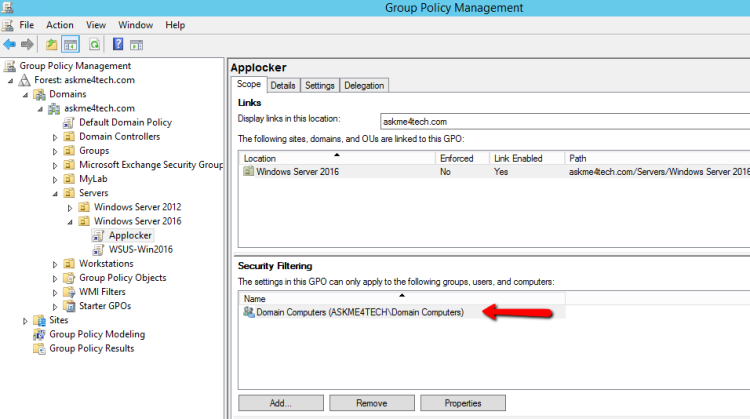
- Now click on the new Policy and in Security Filtering click Add and select Domain Computers Group or any other Group that you have create and include the Servers or Workstations that you would like to deploy it.
- Remember to included in the specific Organization Unit which has Link the AppLocker GPO.
- Unless you must link the GPO in the Organization Units which included all the Server or Workstations that you want deploy the AppLocker.
- Right click in the new Policy and select Edit
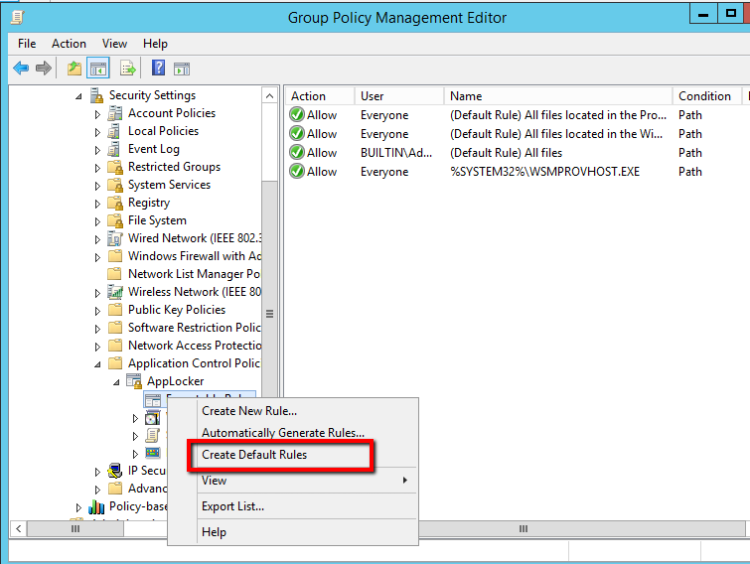
- Go in Computer Configuration\Windows Settings\Security Settings\Application Control Policies\Applocker
- Expand the AppLocker.
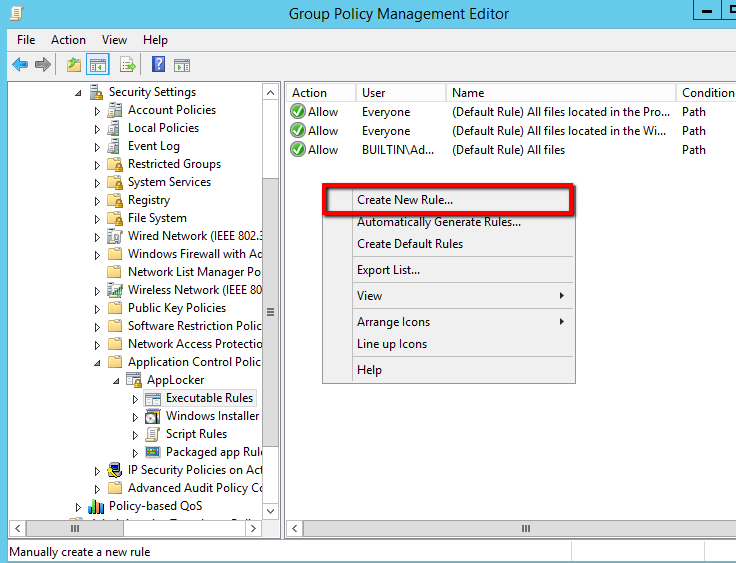
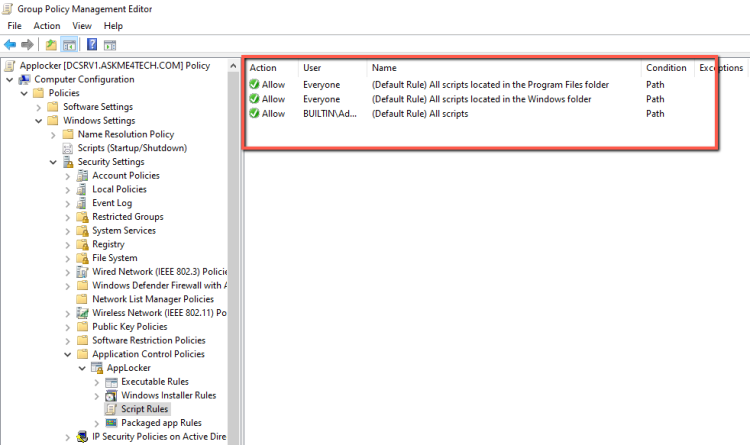
- Right click in Executable Rules and select Create Default Rules
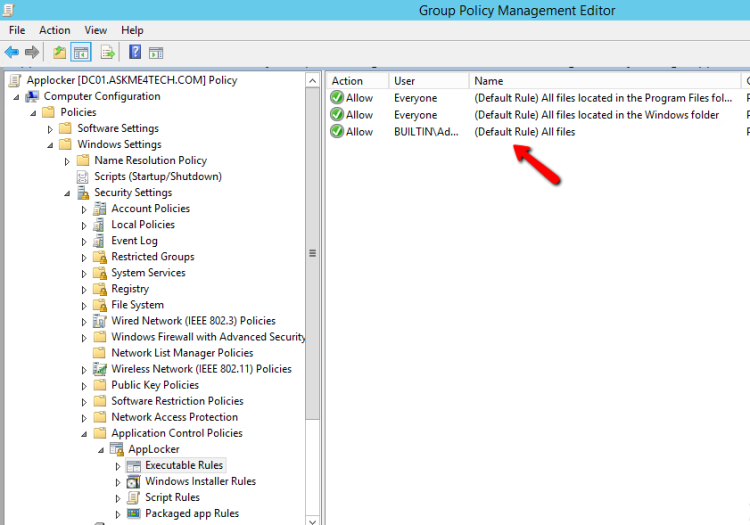
- The Default Rules are
- All files located in the Program Files folder
- All files located in the Windows folder
- All files for the Builtin\Administrators Group.
- Until familiarize with AppLocker It's recommended to create and leave these Rules in the beginning because you don't want to break things.
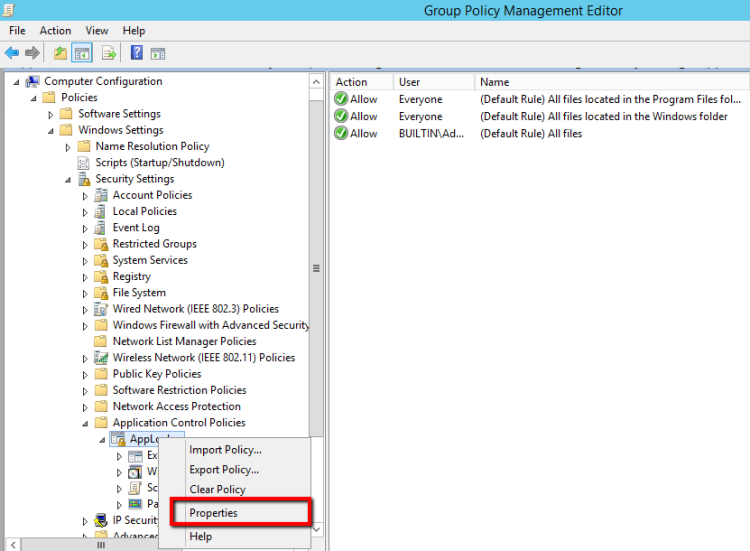
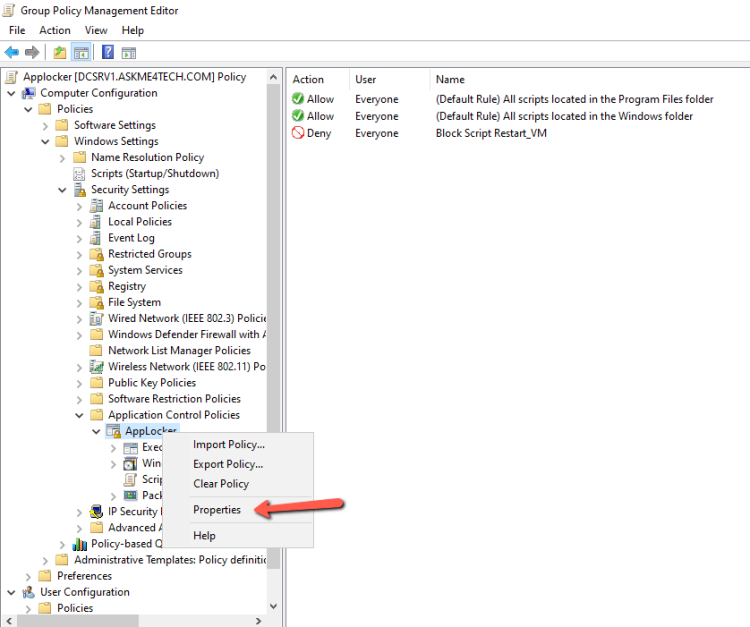
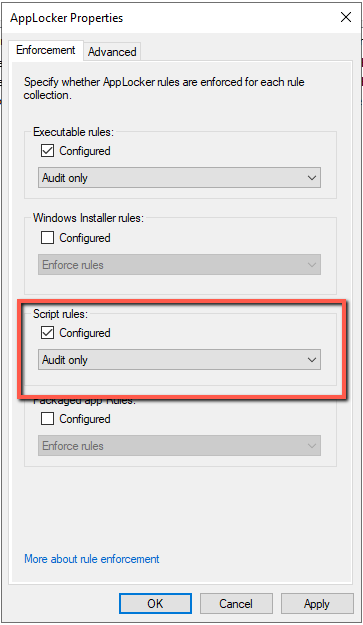
- Right click in AppLocker and select Properties.
- Check the Configured and select the Audit Only.
- The Audit Only mode it's not Allow or Deny just write down Logs in Event Viewer.
- With this way we can identify all the Applications that must run or not before start to Execute Applocker Rules.
How to configure AppLocker Group Policy
We don't want to create any Rule until verify that AppLocker works without problems.
So what we can do ?
We can Deploy AppLocker in a Test Server and not in Production Server until familiarize and identify any issue.
- To run the AppLocker you must start the Application Identity Service in the Server that you would like to deploy.
- In the AppLocker GPO go in Computer Configuration\Policies\Windows Settings\Security Setting\System Services.
- Find the Application Identity Service
- Right click in the Service and select Properties.
- Check the Define this policy Settings
- Check the Automatic.
- Click OK
- Now when you apply the AppLocker GPO the Application Identity service will start.
- Login in the Server that you want to Deploy the Applocker open a Command Prompt and run gpupdate /force
- Restart the Server
How to verify that AppLocker Run in the Server or Workstation
After the server restart we must verify that the AppLocker is run
-
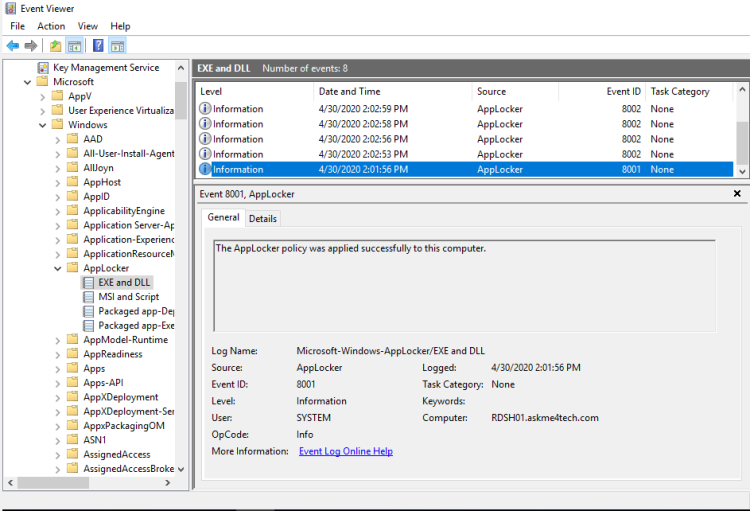
Open the Event Viewer
- Expand Application and Services Logs\Microsoft\AppLocker .
- Click on Execute DLL
- Verify that the Event ID 8001 exist
How to Create an AppLocker Executable Rule
Now that we have see which Application run in our Server we can create the AppLocker Rules that we need.
-
Open the AppLocker GPO
- Right click in Executable Rules and select Create New Rule
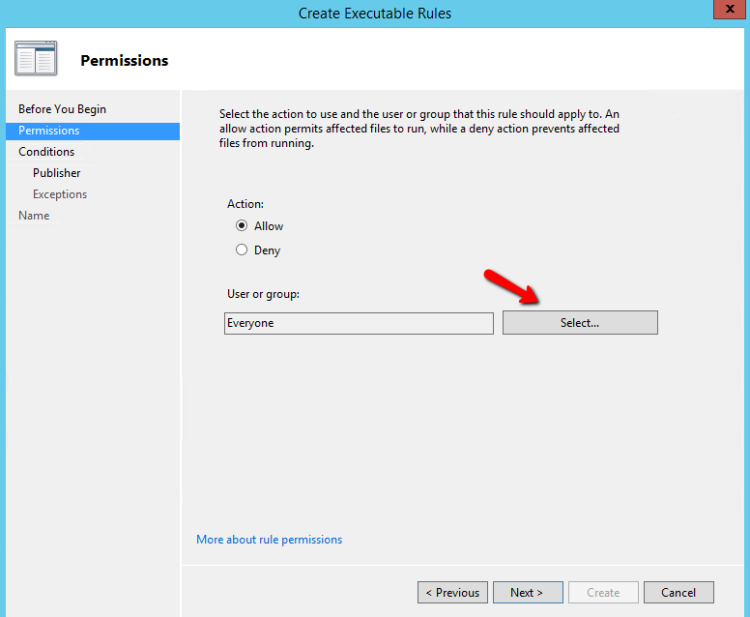
- Click Next
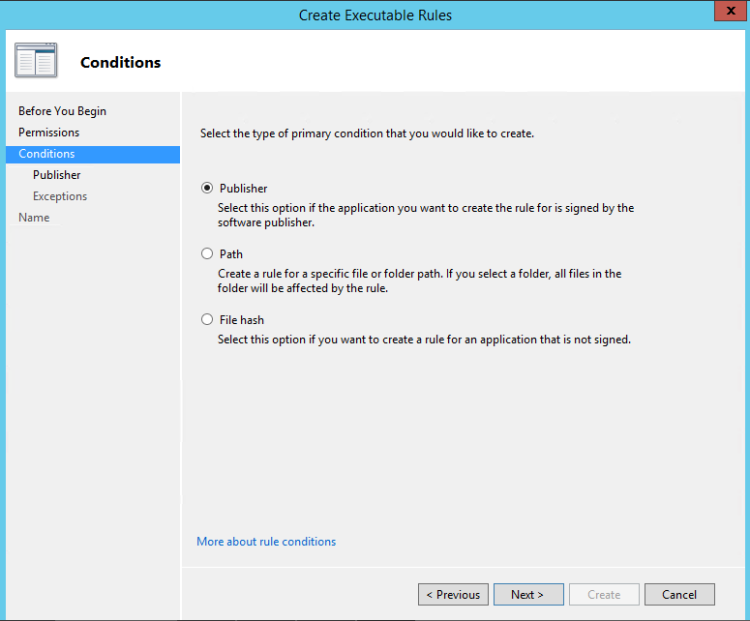
- Identify if you want to Allow or Deny and select the Appropriate Group
- Select how you want to Identify the Application.
- Note that if you select the Path because the Domain Controller will not has the Application to go from Path you can do the following.
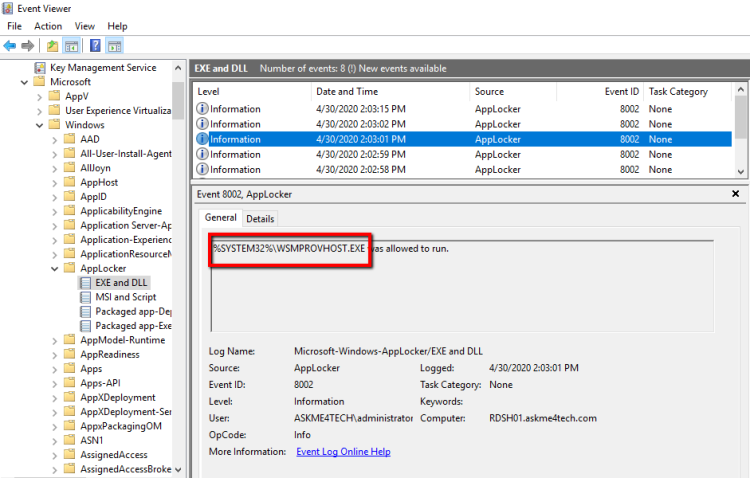
- Open the Event Viewer in the Server or Workstation that run the Applocker and copy/paste the Path from the Logs.
- Now click Next.
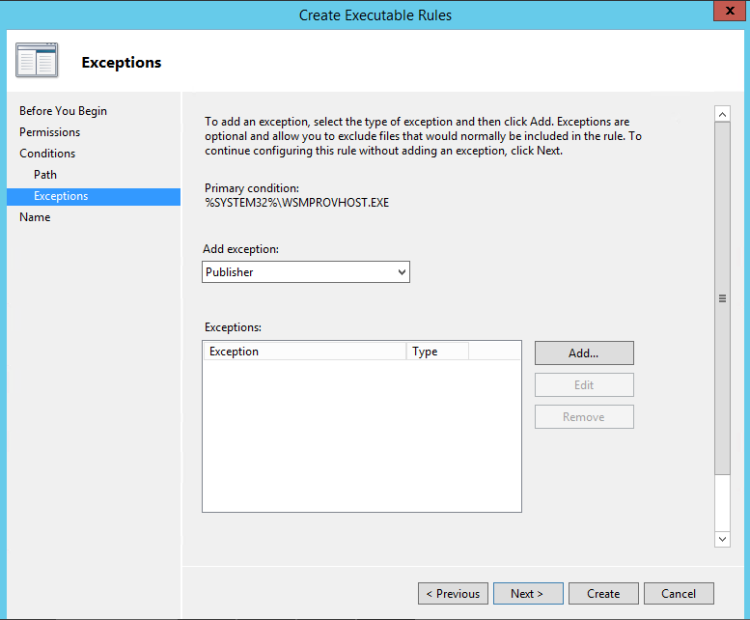
- Again Next except if you want to add an Exception
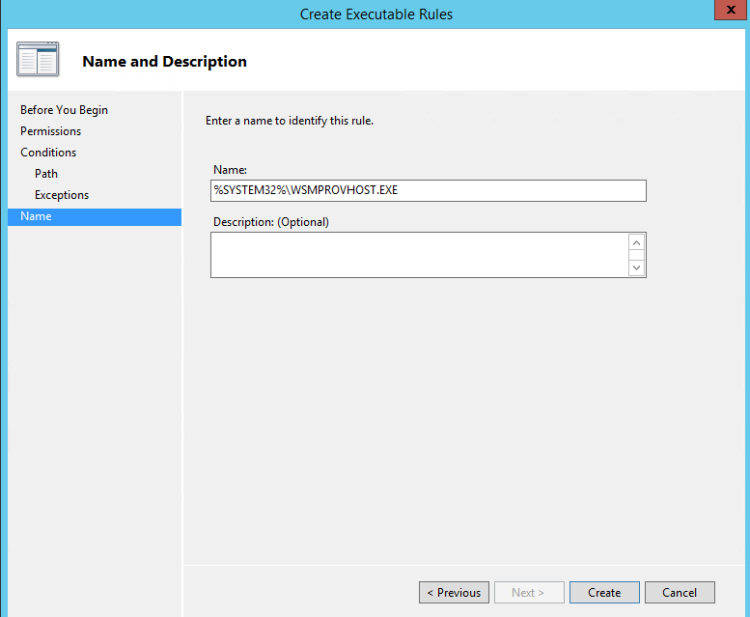
- Type the Name and click Create.
- Go in Server or Workstation and check if the Rule apply
- How to do it?
- Expand Application and Services Logs\Microsoft\Applocker.
- Click on Execute DLL
- Verify that the Event ID 8002 with your application exist.
How to Create an AppLocker Script Rule
We don't want to block only executable files. We would like to block scripts already run in your environment as well.
But let's see important details that we will help us to understand how the AppLocker Script rules are working
AppLocker Script rules include only the following file formats:
- .ps1
- .bat
- .cmd
- .vbs
- .js
In our case, we will try to run a PowerShell command 2from a user after apply the AppLocker Script rule.
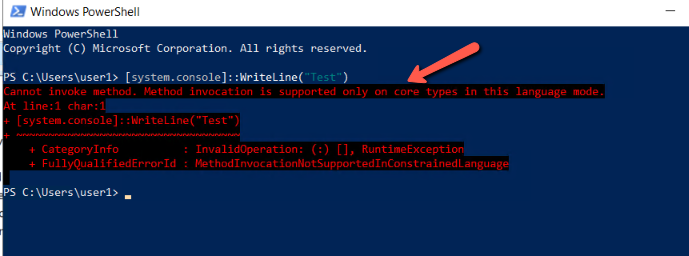
However, when the AppLocker Script Rule have been created the commands or script in PowerShell is still running but only in ConstrainedLanguage mode.
But, what is a Constrained Language Mode?
Based on Microsoft Documentation ConstrainedLanguage mode permits all cmdlets and a subset of PowerShell language elements but limits the object types that can be used.
So, let's start to create the Rules and see how the AppLocker will be behave when we are tying run a PowerShell Script or a command.
- Open the AppLocker GPO.
- Right-click in the AppLocker and click Properties.
- In the Script Rules check the Configured and change to Audit Only. Click OK.
- Right-click in the Script Rules and select Create Default Rules. This step is crucial because it allows the Scripts to run from %Program files% and Windows folders. Windows and Program files folders are running system scripts. If you don’t create the Default Rules then you will break operations in Windows. Servers and Workstations to which the Rule will be applied without the Default Rules will not work as expected.
So let’s see what happens when we run a PowerShell command in a Windows Server that the AppLocker Rule has been applied.
To create our example we will run a PowerShell that I found in the article https://www.techtarget.com/searchwindowsserver/tutorial/Increase-PowerS…
and include commands that will be blocked.
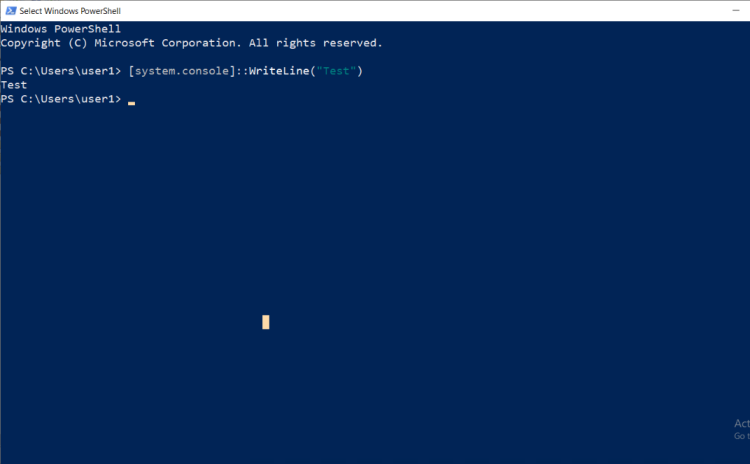
- So, login as a user and open a PowerShell to run a command.
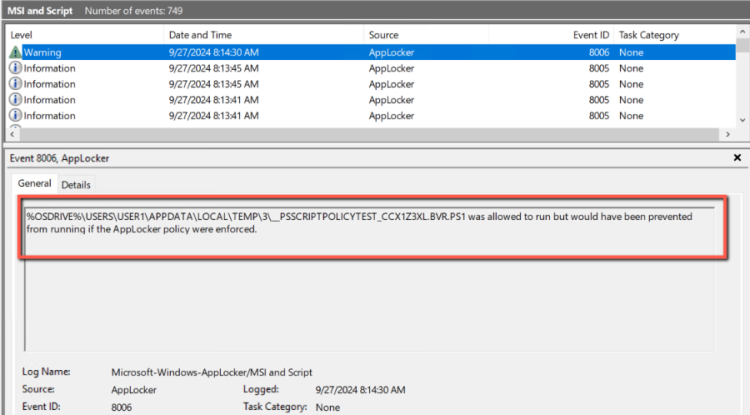
- The script is running. However, let’s go into the Event Viewer to see what we have in Logs from AppLocker. Don’t forget that we are still running in Audit Mode. The only Warning that we have is that the \__PSSCRIPTPOLICYTEST_CCX1Z3XL.BVR.PS1 was allowed to run but would have been prevented from running if the AppLocker policy had been enforced.
- After researching about the PSSCRIPTPOLICYTEST I didn’t find any official documentation from Microsoft. However, from other resources in the following links PSScriptPolicyTest script gets blocked by AppLocker in the event log. Why and what are those files?! from deploymentresearch.com and What are PSScriptPolicyTest Powershell Files? from BROADCOM I found that the PSSCRIPTPOLICYTEST attempted to determine which Language Mode PowerShell will run.
- When we are using AppLocker to block the Scripts each time that will run a PowerShell command or a PowerShell Script the AppLocker blocks the execution in FullLanguage Mode and enables the ConstrainedLanguage Mode in PowerShell.
- Now let’s go to change from Audit Mode to Enforce Rule.
- Run a gpupdate /force. Close the PowerShell and open it again.
- Run the command and you will get an error this time.
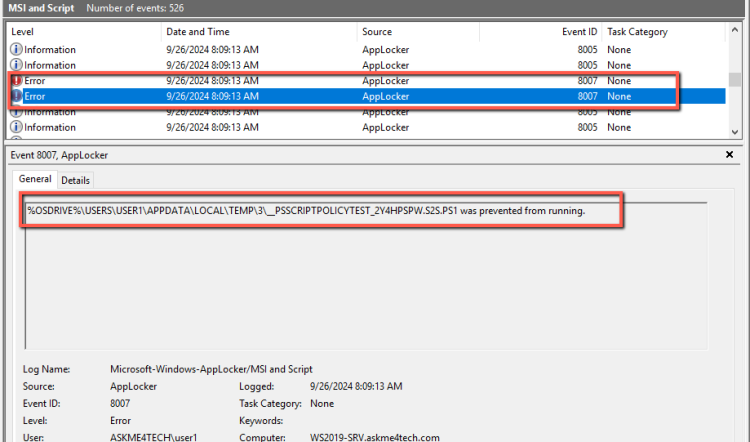
- In the logs we have the following error because we changed it to Enforce the Rule.
\__PSSCRIPTPOLICYTEST_JKNNJVUY.IOT.PSM1 was prevented from running
As we can understand the behavior of AppLocker Script Rules is different from the AppLocker Exec Rules.
We will never see the PowerShell Script name in the Logs.
We will see in the Event Logs only Logs that AppLocker blocking the PSSCRIPTPOLICYTEST which trying to determine in what LanguageMode the script wants to run.
That's it.
AppLocker it's not very difficult to apply.
The difficult part is to be prepare with all the requirements before apply the AppLocker to avoid break things in your environment.
- - > Follow my next article which explain How to collect Applocker Logs from all Endpoints in one place
You can send me an email at info@askme4tech.com or do your comments in Twitter or Facebook
I invite you to follow me on Twitter or Facebook. If you have any questions, send email to me at info@askme4tech.com.