How to integrate BitLocker with Active Directory Domain Services
BitLocker encryption can be integrated with the Active Directory Domain Services. It can be very useful in the scenario that you would like to encrypt all your Devices in your environemnt and store the recovery keys to the Active Directory.
It will be very difficult when you have hundred of devices and you must encrypted, and keep the Recovery Keys in one place. In this scenario the BitLocker Integration with the Active Directory can keep safe the Recovery Keys of each device.
Today i would like to explain how can integrate the BitLocker with the Active Directory Domain Services
Step 1 - Install the BitLocker Drive Encryption Administration utility
I am writing this task as first Step but you can do it in any order.
As usual you can have two different ways to install the BitLocker Drive Encryption Administration utility.
From Server Management
- Open Server Management
- Click Manage -- Add Roles
- Click Next in the the Welcome Screen
- Leave the Role based or feature based installation and click Next
- Leave the Select a server from the server pool and click Next
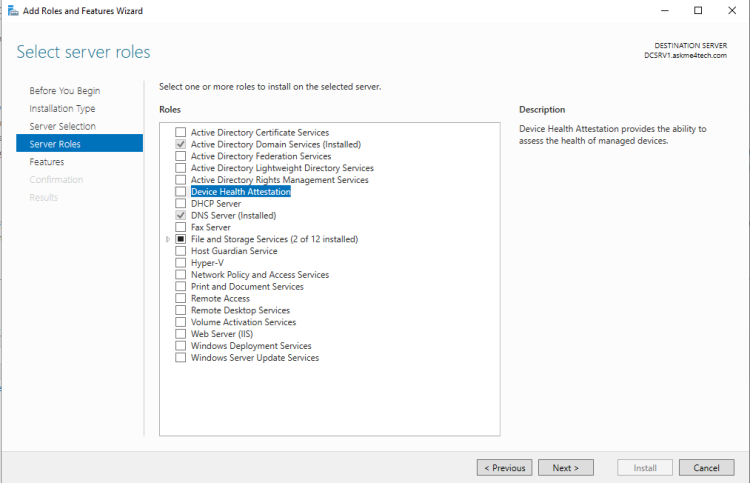
- In the Server Roles click Next
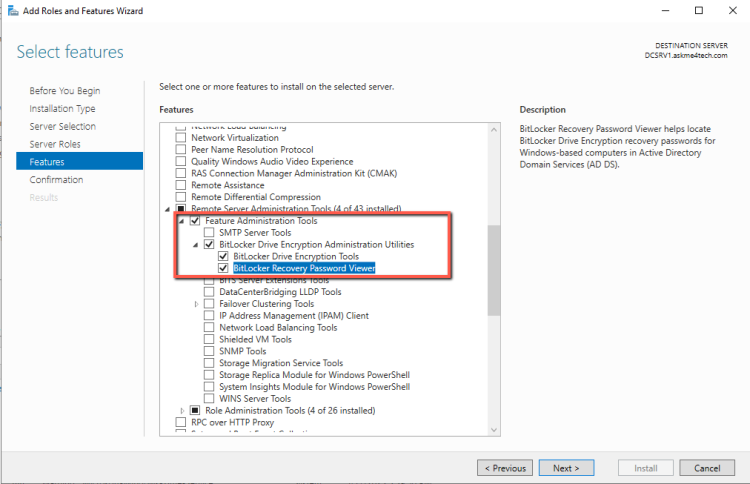
- In the Features Expand the Remote Server Administration Tools and check the BitLocker Drive Encryption Tools. Click Next
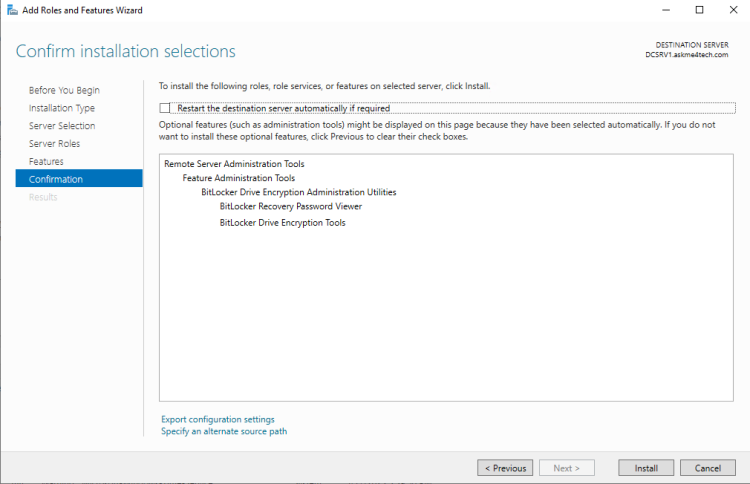
- Click Install
From PowerShell
- Open Powershell as Run As Administrator
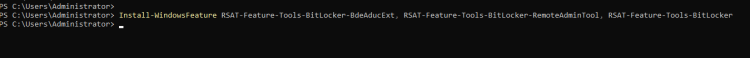
- Run the following command
Install-WindowsFeature RSAT-Feature-Tools-Bitlocker-BdeAducExt, RSAT-Feature-Tools-BitLocker-RemoteAdminTool, RSAT-Feature-Tools-BitLocker
Step 2 - Deploy Group Policy to Store the BitLocker Recovery Keys in the Active Directory
To enable the option in Active Directory and see the BitLocker Recovery Keys you must create and Deploy the following Group Policy.
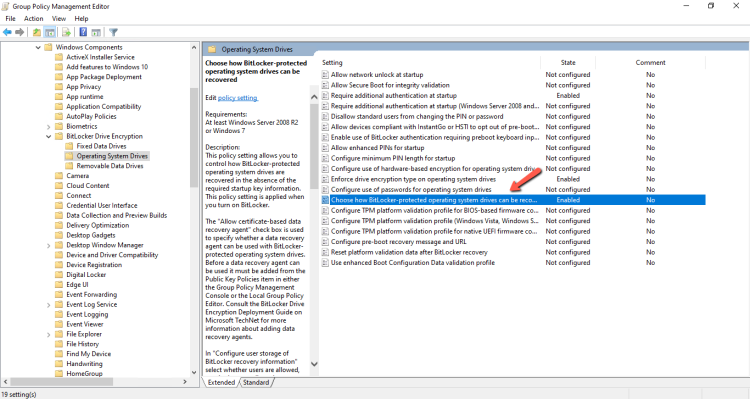
- Open the Group Policy Management Console
- Create a new Group Policy
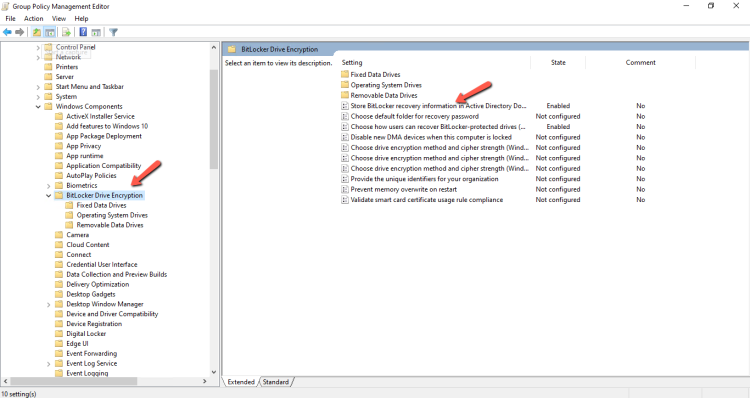
- Expand the Computer Configuration -- Administrative Templates -- Windows Components -- BitLocker Drive Encryption
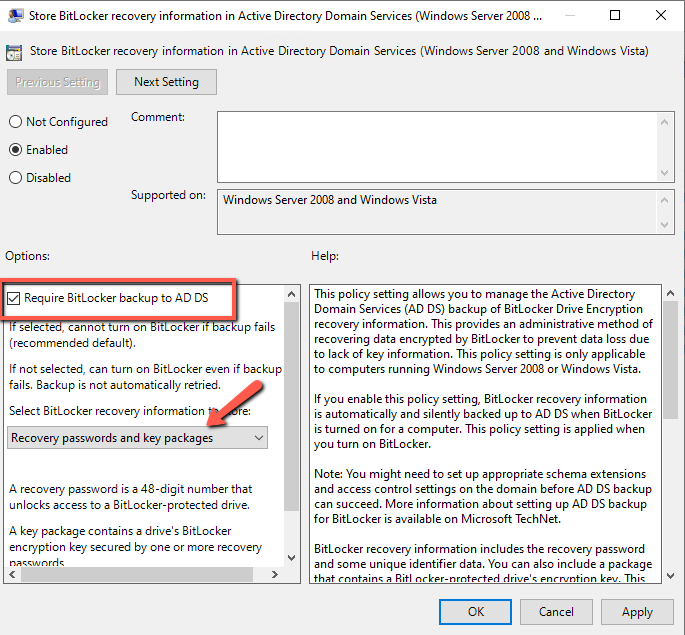
- Edit the Store BitLocker recovery information in Active Directory Domain Services ...
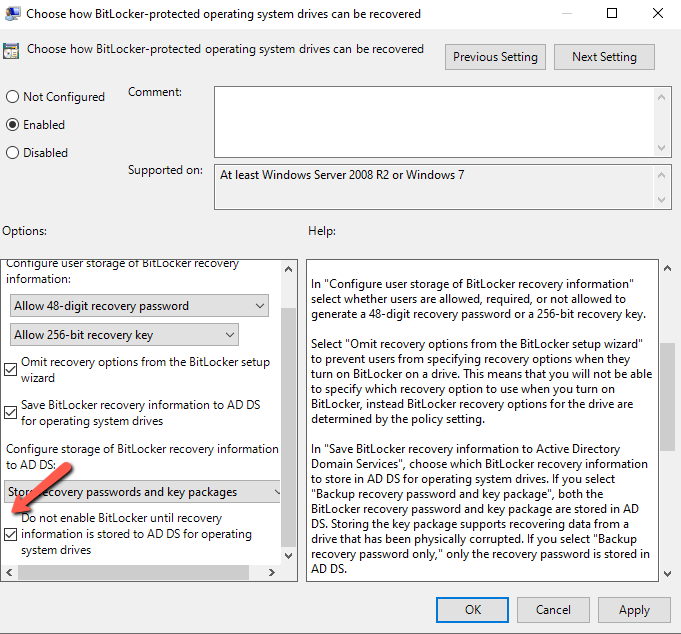
- Enable the Policy and check the Require BitLocker backup to AD DS.(The option ensure that the BitLocker recovery is possible.)
- Be sure that you have select the option Recovery passwords and key packages in Select BitLocker recovery information to store. (This option store the recovery password and the package with the BitLocker encryption key. The key packages can help you to recover the disk when is damaged or corrupted. So it's recommended to keep this option).
If you don't have a TPM in your devices then you must configure the following policy setting as well. Unless the BitLocker will not be enable to the Device that you will apply.
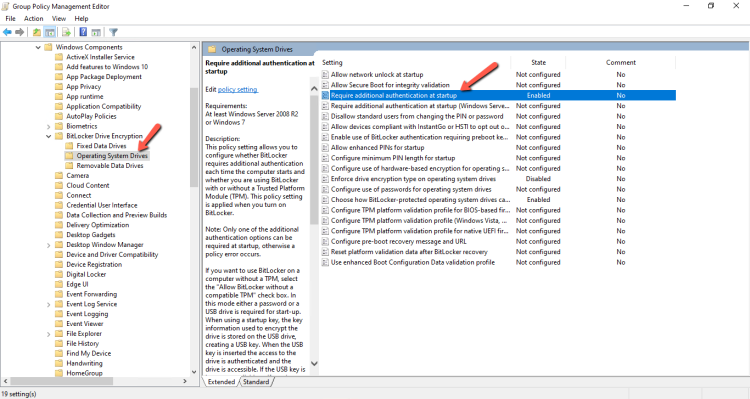
- In the same Policy Computer Configuration -- Administrative Templates -- Windows Components -- BitLocker Drive Encryption click on Operating System Drives
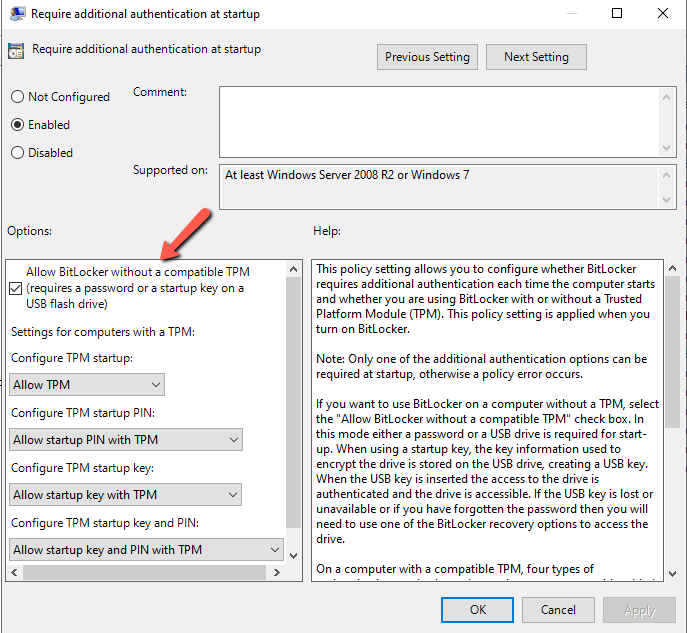
- Edit the Require additional authentication at startup
- Check the Allow BitLocker without a compatible TPM (....) and leave all the settings as it.
However, I would like to explain a few BitLocker Policy settings that can be helpful
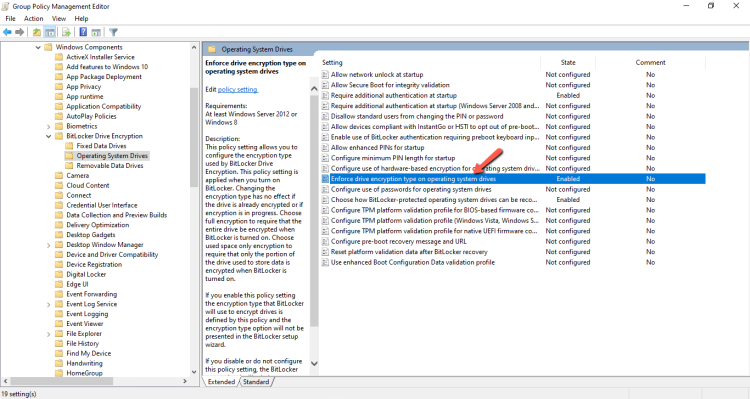
- In the same Policy Computer Configuration -- Administrative Templates -- Windows Components -- BitLocker Drive Encryption click on Operating System Drives
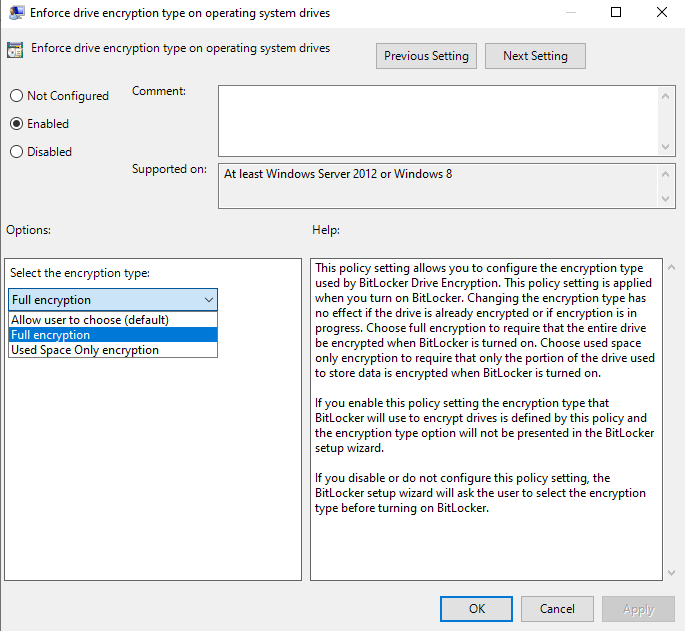
- Edit the Enforce the drive encryption type on operating system drives.
- You can select the encryption type that you want to use in the operating system drives or leave the user to select. For example might be want to use the Full Encryption for all the devices because your policy is to apply BitLocker encryption before give it to the user.
- Another useful policy that you can use is the following.
- Edit the Choose how BitLocker protected operating system drives can be protected.
- You can see different options here but the most important is the Don't enable BitLocker until the information is stored to AD DS for operating system drives. This option can avoid to enable the BitLocker until the device connected to the Domain and backup of the BitLocker information will successfull. So, you can be sure that the recovery can be done in case of any issue with the BitLocker.
Step 3
Verify the Results