How to Protect File Servers from Ransomware
After so many years Ransomware still is one of the most dangerous mailware . Today users are more carefully , lot of monitoring tools can be found in the market against ransomware. However lot of companies are still infected with Ransomware.
New types of Ransomware born very often and the protection continues to be very difficult task. Cases of ransomware infection were first seen in Russia between 2005 – 2006. Trend Micro published a report on a case in 2006 that involved a ransomware variant (detected as TROJ_CRYZIP.A) that zipped certain file types before overwriting the original files, leaving only the password-protected zip files in the user’s system.
What is Ransomware
Base of Trend Micro << Ransomware is a type of malware that prevents or limits users from accessing their system, either by locking the system's screen or by locking the users' files until a ransom is paid. More modern ransomware families, collectively categorized as cryptoransomware, encrypt certain file types on infected systems and force users to pay the ransom through certain online payment methods to get a decryption key.>>.
How can infected from Ransomware
Ransomware spreads through email attachments infected program or infected websites. If a user click on the attachment then the Ransomware activated and it starts spreading across the system or network depends from the type of Ransomware.
Finally locks the System or encrypt your files and ask a certain amount of money to provide the access in your system or decrypt your files.
Precautions against ransomware.
You can protect from Ransomware attacks with different ways but the most important is BACKUP BACKUP and BACKUP. If you have updated backup in a worst case scenario you can restore your files and loose only few hours of work in worst case.
To prevent ransomware attack and keep it away i have write some steps that can follow
- Keep your Windows up to date.
- Keep your Antivirus up to date.
- Don't open email attachments that you aren't sure.
- Disable Remote Desktop feature whener you can.
- Avoid browsing websites that are often the breeding grounds for malware such as illegal download sites, porn sites and gambling sites.
- Training your users.
Today i would like to explainn how can protect File Servers from any type of Ransomware with the FSRM (File Server Resource Manager).
Let's start to prevent the Damage!!
For the solution will use File Server Resource Manager (FSRM) and Powershell.
How to install File Server Resource Manager
- Open the Server Manager
- Click the Add Roles and Features.
- Click Next in Welcome Screen.
- Select Role-based or feature based installation.Click Next.
- Use the default options and click Next.
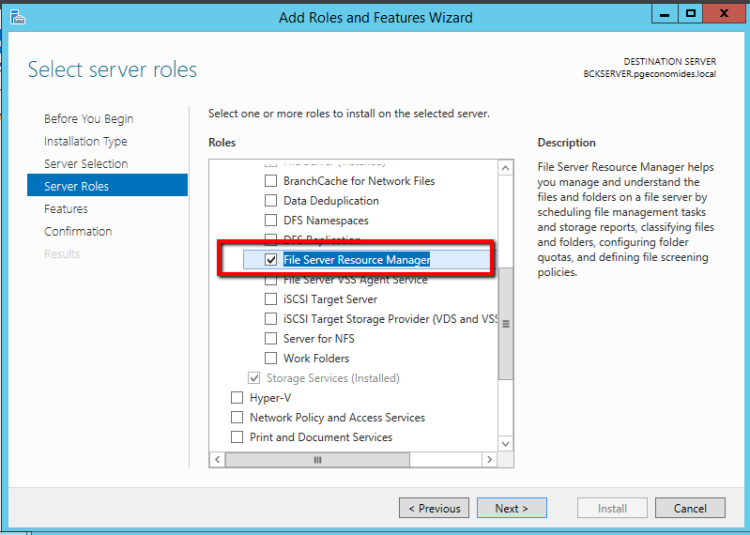
- Expand File and Storage Services - - > File and iSCSI Services.
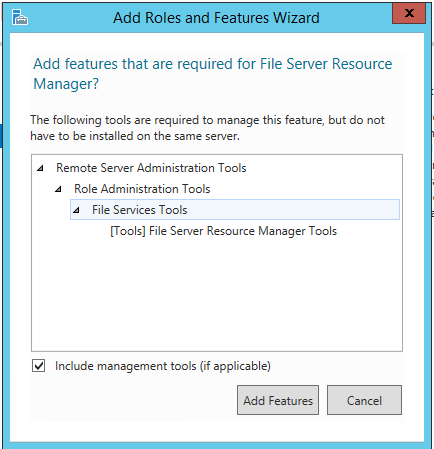
- Select File Server Resource Manager.Click Add Features and Click Next.
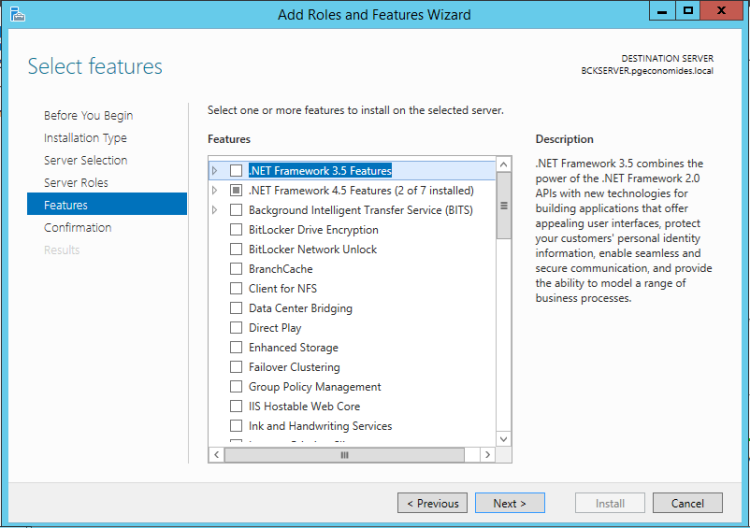
- Don't change anything and click Next.
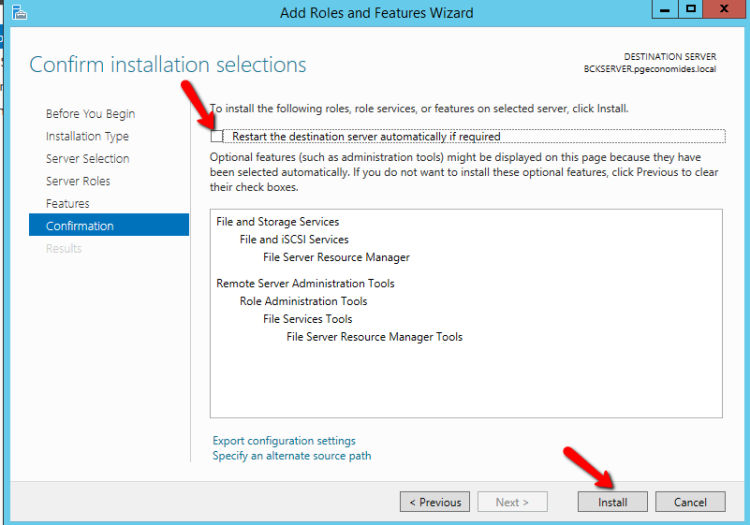
- Click Install to start the Installation and Wait to Finish.
How to Create a File Group
After the installation has finished the first step is to create a new File Group as follow
- Open the File Server Resource Manaager
- Right click in the File Groups and select Create a File Group.
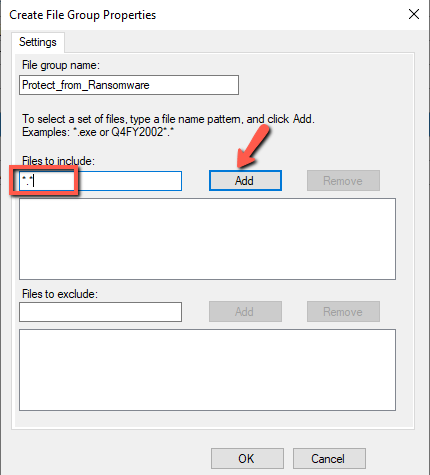
- Type a File Group Name. I typed Protect_from_Ransomware.
- In the Files to include type * . * (all the files) and click Add and OK.
So now we have create the File Screen Group with name Protect_from_Ransomware. that will be use it in next Step.
How to create Create a New File Screen
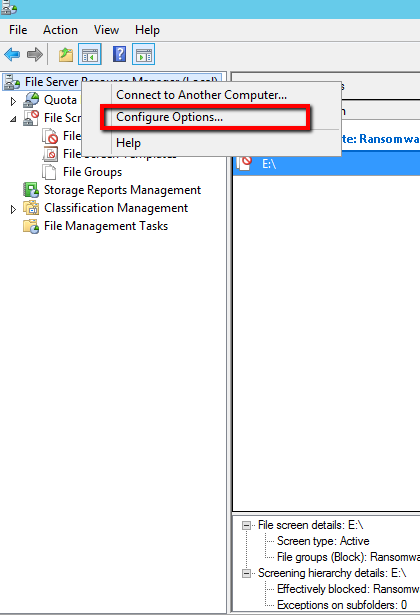
- First of all must configure FSRM to send email notifications so open File Server Resource Manager.
- Right click in File Server Resource Manager and select Configure Options.
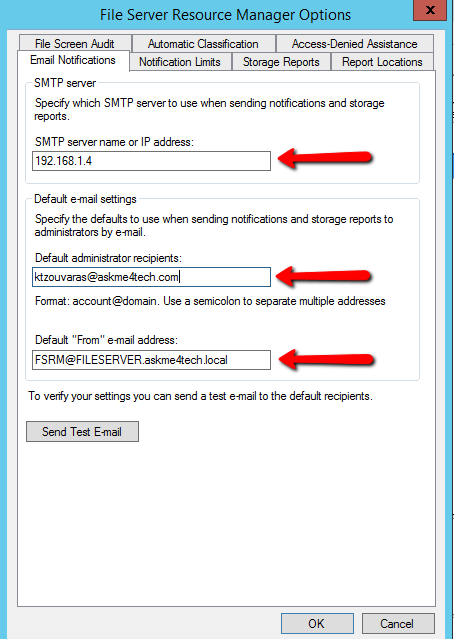
- Fill the SMTP Server and Default Administrator Recipients. Click the Button Send Test Email to verify that receive emails from FSRM.
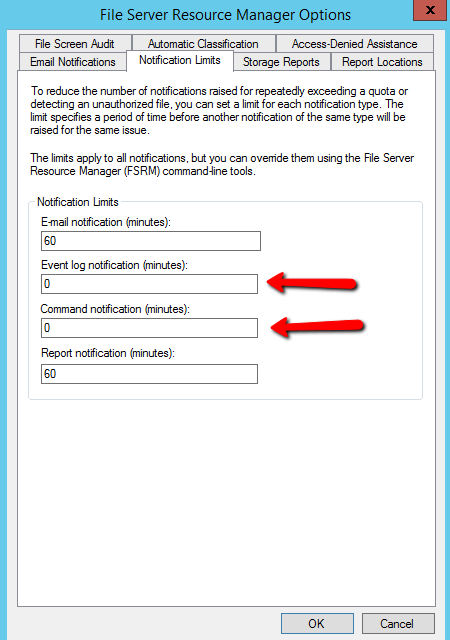
- Click in Tab Notification Limits and change Event Log Notifications (minutes) and Command Notifications(minutes) to 0. Click OK
- Right Click in File Screens and Select Create File Screen.
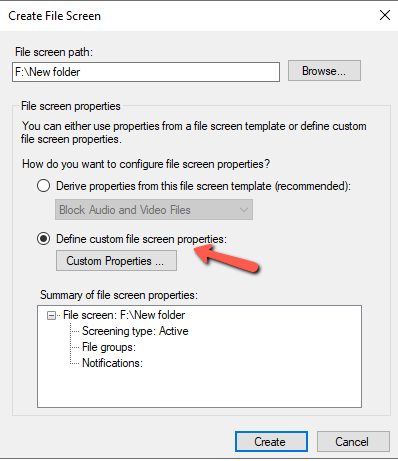
- Select the File Screen Path which is the Folder or Drive to monitoring for any incident base on the Protect_from_Ransomware. Group that create in previous Steps.
- Select Define Custom file screen Properties and click in Button Custom Properties
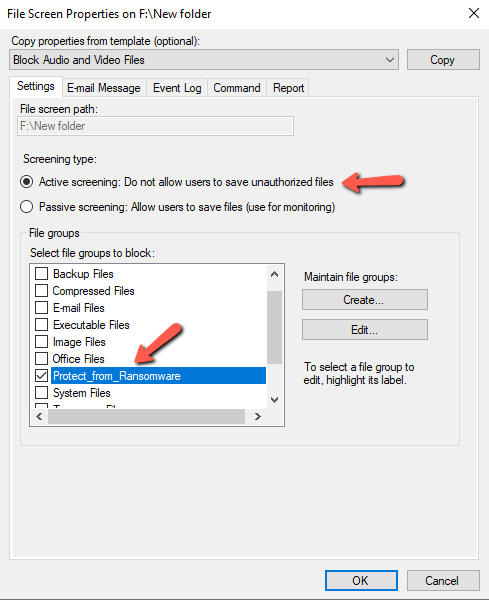
- In the Screening Type select Active Screening: ..............
- In the File Groups select Ransomware_Extensions. This is the File Group that we have created above.
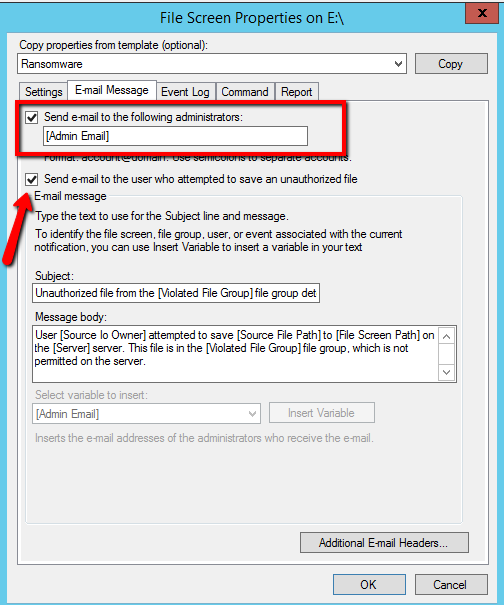
- Go in Tab Email Notifications and check Send e-mail to the following Administrators and Send e-mail to the user that attempted to save and unauthorized file.
- Click OK to create the File Screen.
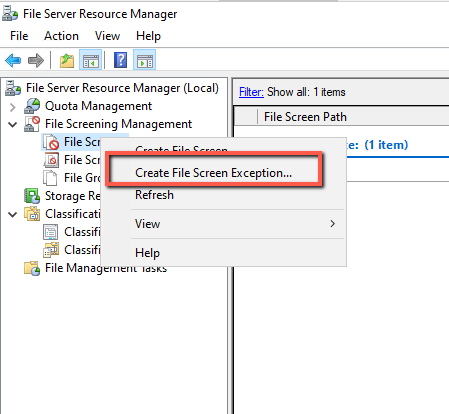
How to create a New File Screen Exception
Because we have created a File Group to include all the file extensions we should create a File Screen that will be exclude the file extensions that we use it daily in our File Serverr.
- Right click in the File Screens and select Create File Screen Exception.
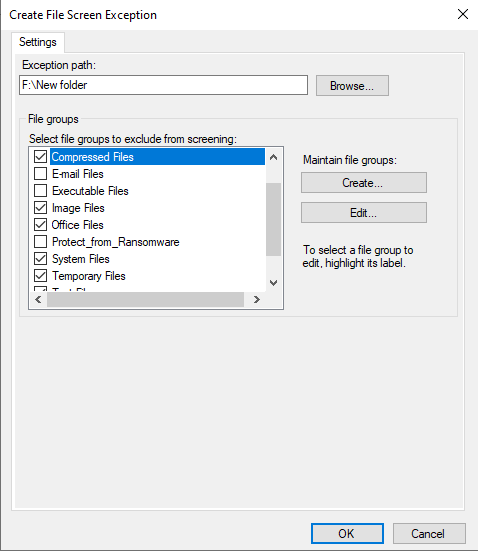
- Select the File Screen Path which is the Folder or Drive to monitoring for any incident.
- In the File Groups select any extension that you would like to exclude.
- For the scenario i have selected the most common extension in a file Server like Compressed files ,Image files ,Office Files, Text files and click OK.
- Depends on your requirements you can select the appropriate file extensions.
Verify that the File Screen works
We have completed the configuration and it's time to tested
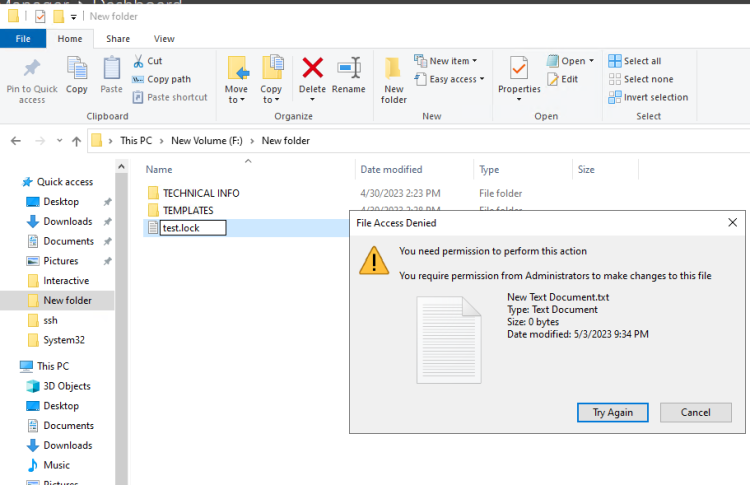
- Open the folder that you have enable the file screen and create a test Document. Change the extension of .docx to .lock or any other extension except those that you have exclude.
- If the configuration is correct you will not allow to change the file with the Warning and you will receive an email notification too.
- That's it !!
We know that Ransomware it's not effected only File Servers today. However with FSRM you can create another one security level to protect your File Servers and prevent any damage that you will cause a downtime of some hours until multiple days.
Have a nice weekend!!